Analyzing PCAP Files with Wireshark on NoBrowser’s Phishing Sandbox as a Service
Analyzing network traffic is crucial for identifying security threats...
 ProtectingYourself Online
ProtectingYourself Online
Topic: Safe Phishing Detonation using Phishing Sandbox
Overview:
As we know, phishing is still a prevalent method of compromising one’s computer and statistically the most common attack path to corporate networks. According to Verizon’s 2022 Data Breach Investigation Report (DBIR) 82% of attacks in the past year stemmed from social engineering, a majority of those being phishing. In this blog post, I will show you how easy it is to get phished – I will dissect a phishing attack end-to-end in an ephemeral sandbox, to show how easy you could be compromised.
Today, I received a juicy phishing email claiming to be from Coinbase. Typical with phishing attacks, the attacker instills a sense of urgency. In this case, the email states that a withdraw from my Coinbase account has been initiated. As you see, the source email address looks suspicious (from no-replycolnbase@claire wordley[dot com]), lets dive deeper.

#WARNING – DO NOT CLICK THIS LINK#
I view the email in my local web browser and right click on “View withdrawal” and ‘copy link address’. This copies the link to my clipboard, it does not detonate the link on my local computer.
**DO NOT ACCIDENTALLY CLICK ON THIS LINK!**

I then go over to my Phishing Sandbox at NoBrowser.com and launch Chrome and Fiddler (a pre-installed web inspection tool). NoBrowser offers ephemeral Phishing Sandboxes, which come with preinstalled browsers and tools. They provide real, ephemeral Windows instances, so if it gets infected, the session is forensically destroyed when you Log Off and a new golden copy is ready upon next Login. With that said, I feel safe testing here, lets proceed.

I still have the phishing link in my local clipboard, so I then paste it to my NoBrowser session.
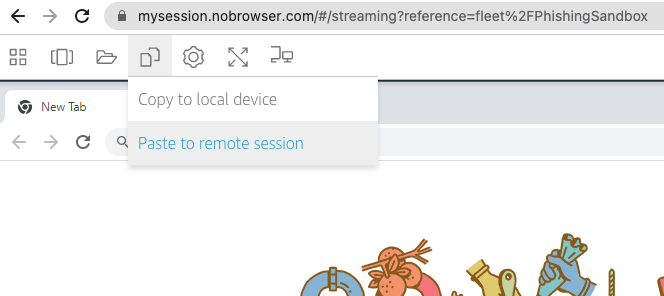
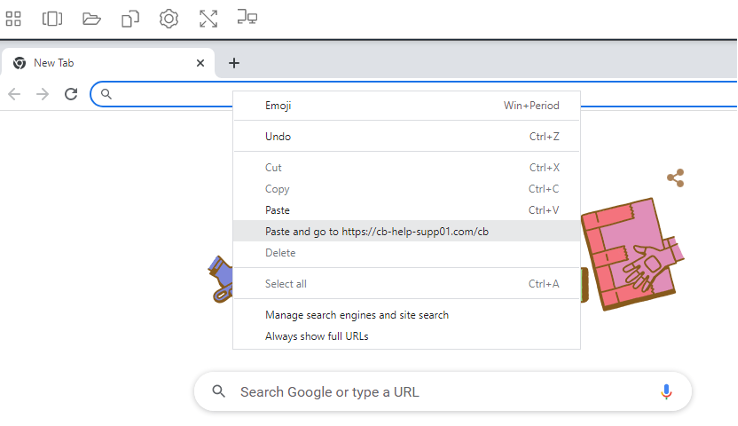
Here is where it gets interesting. Inside of your session, go to Chrome, right click, and paste the link. Notice the URL is clearly not Coinbase, as claimed in the original email.
While visiting the link in Chrome, I view Fiddler on the right side of my screen. Fiddler shows I now have a connection to various domains, including vkontakte[do.t]ru, vk[do.t]com, vk[do.t]cc, and others which are all clearly not Coinbase. So far looks like I *may* be in trouble, lets continue to dive deeper.

I pop open a cmd prompt in my session and enter ‘netstat -ano’ to show active and listening network connections, including those ESTABLISHED. A few IP’s look abnormal, lets further investigate 93.186(dot)255[dot]194. It appears that this remote host has an encrypted connection with my machine over SSL 443.

In researching this address, I see that I now have an established, encrypted session to a server in R.u.s.s.i.a. I venture the guess that this is not Coinbase. This validates the crafty but suspicious email I received from ‘Coinbase’ was far from legit.

When I am done analyzing this Phishing link in my NoBrowser session, I simply click ‘End Session’ and the instance is automatically torn down & wiped, and a new golden copy ready for me during my next login.


"now I see an established, encrypted session to a server in..."
Catch you next time – Happy Hunting!
🛡️🌐 #CyberSecurity #OnlinePrivacy #NoBrowser
Analyzing network traffic is crucial for identifying security threats...
Worries of public Wi-Fi networks and confidently accessing...